As already predicted in a previous post about Conti, it did not take long for them to reappear in the spotlight of the news. Last week the ransomware gang claimed to be responsible for the cyberattack that hit a German manufacturer of wind turbines, Nordex. This attack happened on March 31, 2022. Nordex shut down its IT systems across multiple locations and business units as a preventive measure, trying to prevent the threat to spread across their networks. This week, Nordex announced that it was working on fully recovering operations after the attack.
However, other news appeared this week about a hacking group (NB65) that used Conti’s leaked ransomware source code to create its own ransomware that the group uses in cyberattacks against Russian organizations. NB65 has already breached Russian entities, stole their data, and leaked the data online. The group warns that the attacks are because of the invasion of Ukraine.
Most antivirus vendors detect the sample that NB65 used for its Ransomware on VirusTotal as Conti. Intezer Analyze also determined that it uses 66% of the same code as the usual Conti ransomware samples: no doubt that NB65 used the source code.
In this post, I will explain how the Conti Attack Kill chain works. A kill chain is a chain of phases of a cyberattack from early reconnaissance to the goal of data exfiltration.
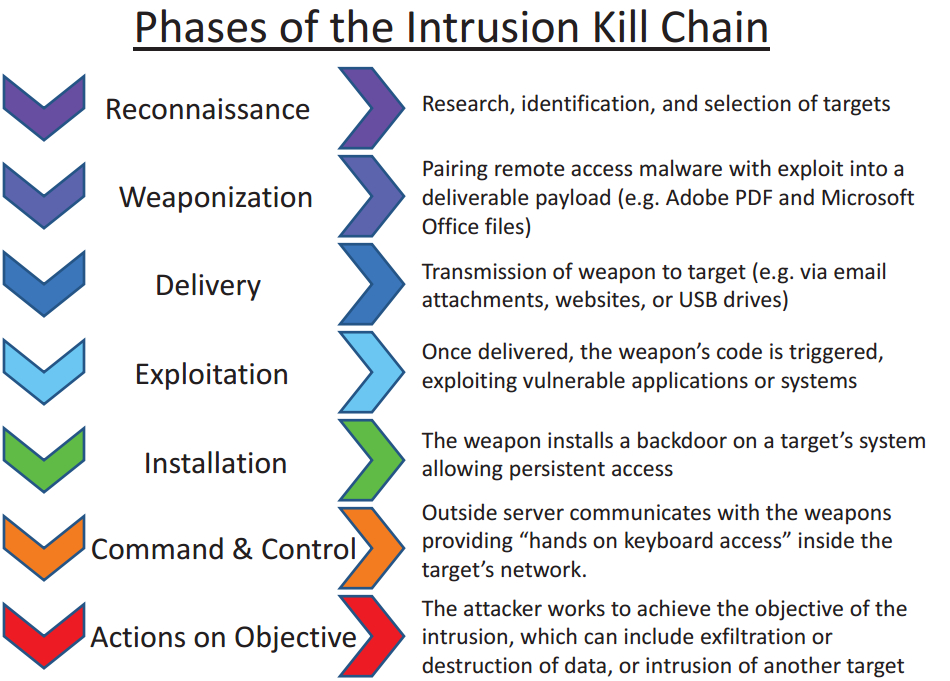
The ransomware that Conti uses is changing its attack pattern daily: it is extremely dynamic which makes it very unpredictable. It relies on the most recent security exploits, of which there are two main ones:
- PrintNightmare (CVE-2021-1675, CVE-2021-34527, and CVE-2021-36958) works by escalating the Windows Print Spooler service permissions to executive privileged operations. An attacker can use this exploit to install programs; view, change, or delete data; or create new accounts with full user rights.
- FortiGate firewall remote code execution (CVE-2018-13379 and CVE-2018-13374) is a buffer underwrite vulnerability that impacts FortiGate VPN servers to gain access to enterprise networks.
Patching is an important task for a system administrator and an important defense mechanism against cyberattacks. However, Conti knows that over 60% of all the companies do not have a state-of-the-art patch management system in place. This means all these companies do not update their security patches frequently. Conti’s affiliates anticipate users that wait for days, weeks, or even months before they download and run security patches. For attackers, it is possible to compromise unpatched systems within hours after software manufacturers release a patch. This is because of the high automated Ransomware as a Service (RaaS) business model that Conti uses.
Target selection
As stated before, the RaaS service model gives Conti’s affiliates flexibility in the way they choose to operate. Conti affiliates use a wide range of target selection methods, including:
- E-mail phishing
- Mass vulnerability Scanning
- High-end malware distribution software
- Credential stuffing
- Fake websites, impersonated phone calls, and similar social engineering tactics
E-mail phishing is by far the most common method that Conti affiliates use. Another method Conti affiliates use is the one of mass vulnerability scanning. Mass vulnerability scanning relies on automated bots that check publicly exposed networks for known vulnerabilities. Conti affiliates also use high-end malware as a service (MaaS). Examples are Emotet, Trickbot, and BazarLoader.
How does the Kill Chain work? A Practical Example
An attack kill chain can begin with a phishing campaign. This installs, for instance, the Trickbot backdoor onto target systems. A phishing campaign often takes advantage of Microsoft Office, Google Docs, or Adobe Acrobat links that are sent by e-mail. Attackers use these links to redirect victims to malicious sites where they then download the TrickBot payload: a payload is the component of the attack which causes harm to the victim.
When a victim has downloaded the payload, the reconnaissance phase begins. During this phase, the ransomware tries to discover all directories and network shares inside the system of the victim. From there it expands.
Before the attacker launches the Conti ransomware, they often try to identify mission-critical systems like domain controllers or backup servers:
- Domain controllers are important to an attacker because they control access to the entire network. Successfully hacking a domain controller gives the attacker access to all domain network resources, including the authentication credentials for all users in the domain.
- Backup servers are important for an attacker because it is the last line of defense for a defender. When an attacker can get access to this last line of defense it can delete all files on the backup servers as well, making price negotiations much easier with an infected company because they do not have a copy of their encrypted data.
If an attacker can find the domain controllers and the backup servers in the beginning phase of the kill chain, the attacker can trigger the next phase of the attack quicker.
Once the discovery and reconnaissance phase is complete, the data exfiltration phase begins. Conti attackers evaluate the data inside the victim’s system. After evaluation, they decide whether it is important for the target company. If the data is important enough, an attacker will start exfiltrating the data to an anonymous account on the cloud-based anonymous file upload service called MEGA. The tool that an attacker uses to upload the data to MEGA is a software tool, named rclone. Rclone is an open-source, multi-threaded, command-line computer program to manage or migrate content on the cloud and other high latency storage.
After the attackers complete the first two stages successfully, Conti starts to encrypt all files and backups in the system of the target company. This also includes accessible network devices. Accessible network devices enable communication with network equipment and services in Wide Area Networks (WAN) over a physical connection, and/or between Local Area Networks (LAN) connected to data network devices (e.g., PCs) and network equipment and services in Wide Area Networks (WAN) over a single physical connection. Examples of network devices are Routers, Modems, Hubs, Gateways, Hotspots, and Switches.
Conti Ransomware uses ChaCha8 encryption. ChaCha8 randomly generates keys for each target system. Every key that ChaCha8 generates is encrypted with an RSA-4096 public key and is stored at a specific, offset of each file. Attackers use these keys to identify the victim, manage negotiations with the victim and eventually generate decryption codes once the victim pays.
The Demand and Negotiation Phase
If the attackers have finalized the ransomware execution phase, all the important files of the victim are encrypted by ChaCha8, backups are deleted and a readme.txt file containing the ransom note is dropped on the desktop of the target system.
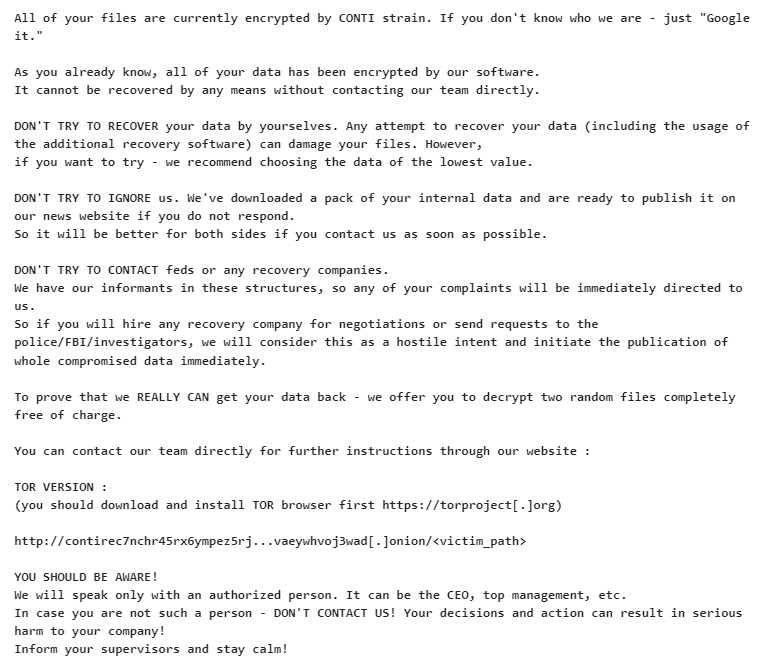
The ransomware note has a direct link to a victim-specific chat portal. The Conti portal contains a landing page that instructs the user to follow the instructions in the README.txt file that is written to disk after file encryption.
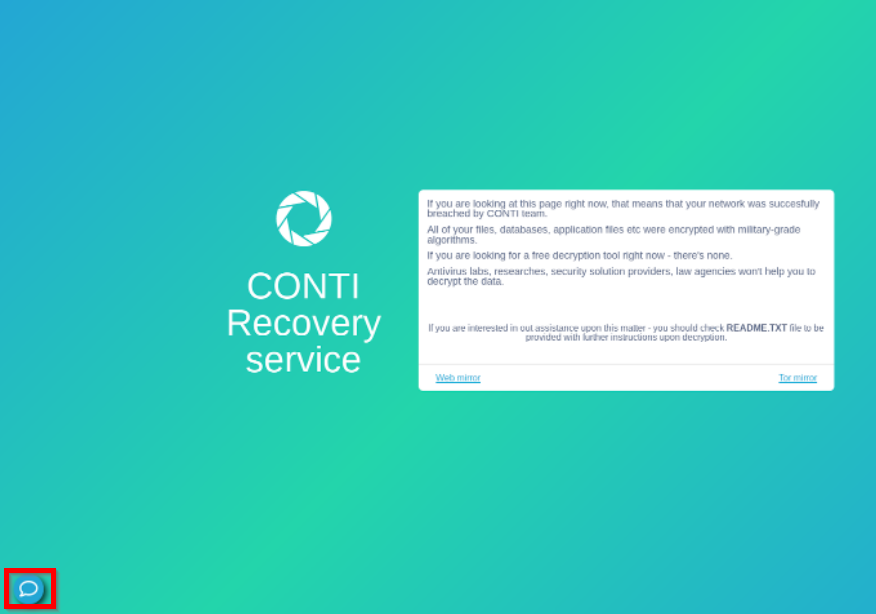
When the victim contacts the Conti Recovery Service, the Conti affiliate sends the total captured file size and enumerated system information to the user. Conti affiliates do this to prove that the data was compromised and that the data is in Conti’s possession. The February 2022 leak also provided chat files, which give clear insight into how Conti operates and how their communication with a victim is done.
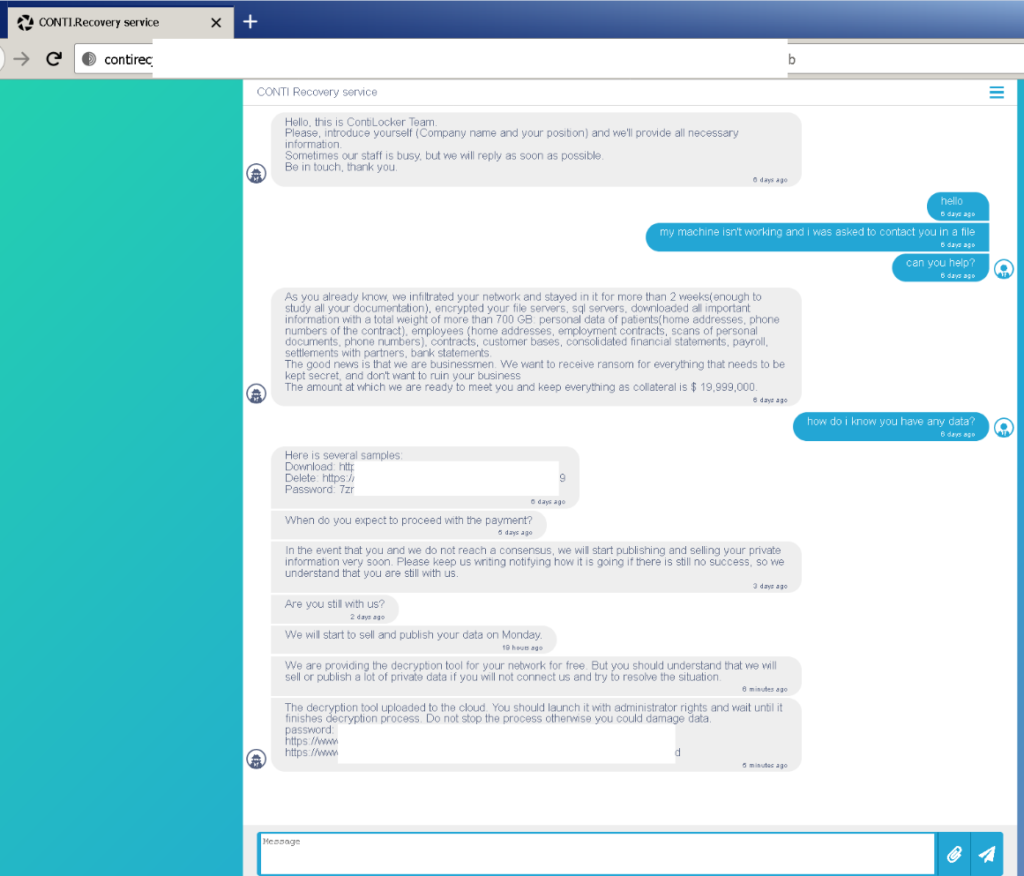
After the attacker and victim have an agreement, the victim sends bitcoin to the designated address and the attacker produces a decryption key using the victim’s ID. However, there are Conti affiliates that simply take the cash and disappear, refusing to provide the decryption key as promised: it is not a 100% guarantee that the victim receives back its files.
If the attacker sends the decryption key to the victim, the link also includes a user manual. The manual explains how to use the decryption application. All information that is retrieved by the Conti affiliate from the victim’s system is uploaded to a free file-sharing site where the victim can retrieve the information and delete it from the sharing site after retrieving it.
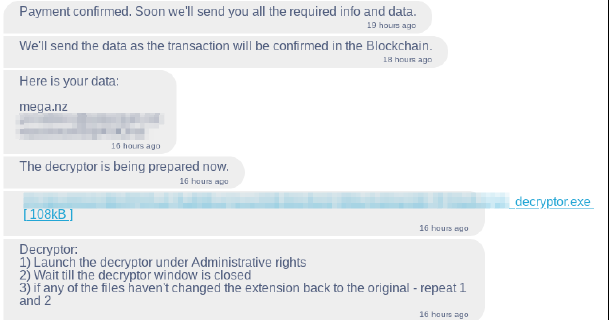
After Payment Process
As an extra service, Conti affiliates will also send a recommendation message in the chat with the victim, providing advice on how to protect against future attacks:
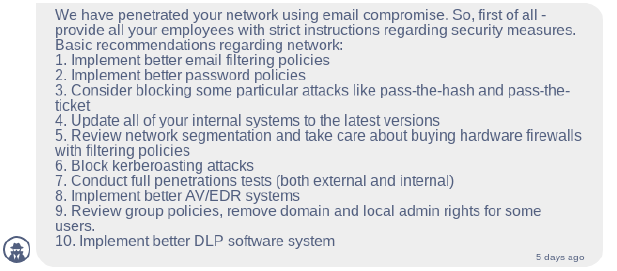
Final Thoughts
Although Conti’s source code and chat logs were leaked in February 2022, Conti continues to conduct ransomware attacks against big organizations. The expectation is that Conti will update the malware and will potentially rebrand the source code leaks that have damaged its reputation and which may lead to criminal groups forking the code. Forking means that other parties created a new product based on the current source code. As seen in the introduction of this post that already happened and the expectation is that more parties will further develop the leaked code into new ransomware products.
It is important to know how Ransomware works and how it looks to arm yourself against any form of panic when an attack happens. Once you know what a ransomware attack looks like, you can manage the situation in a rational way. This is important: panic can only result in collateral damage on top of the initial attack.
Another lesson we can learn is that phishing is still the most common method that attackers use to get inside the system of a victim. This confirms the importance of continuous security awareness training for employees inside an organization.
Feel free to contact me if you have any questions or if you have any additional advice/tips about this subject. If you want to keep in the loop if I upload a new post, do not forget to subscribe to receive a notification by email.





