As already mentioned in last week’s post despite the recent leak of internal communications and code from the Conti ransomware group, at the start of the Russia – Ukrainian war in late February 2022, Conti continued operations without breaking stride, in part thanks to constant technological innovation.
In my previous posts, I provided info about how Ransomware attacks work in general, the history of the (currently) biggest Ransomware group Conti, and how Conti’s Kill Chain Attack works.
In this post, I will focus on how Conti manages their affiliates/employees (including their flow of money) and its ransomware technology.
Stronger than ever
In 2021, an average of 43 victims per month were reported on the Conti leak site. In November last year, a peak was reached of 95 before falling down because of the winter holidays. This shows that Conti operates like any ordinary business where employees are celebrating winter holidays as well. Activities started up in January and February again and had a big increase in March 2022. Despite public disclosures, the number of Conti victims posted in March surged to the second-highest monthly total since January 2021. This means Conti continued and even increased the tempo of its operations without disruption.
43 victims per month seem pretty low but don’t forget that the biggest part of its victims is not listed on the Conti data leak site. Max 20% (but lower most of the time) of ransomware group victims ever get listed on a data leak site, if the group uses one. Conti uses a “forked” strategy. When applying this strategy, attackers will demand a ransom payment for decrypting data, and threaten to publicly publish sensitive data if the ransom is not paid by a certain deadline. This strategy is also called ”Double Extortion”, meaning it often steals data from a victim before crypto-locking systems and then demands a ransom not just for a decryption key, but also a promise from the criminals that they won’t publicly leak or sell the stolen data to others. Victims who don’t quickly meet Conti’s ransom demand often get named on their dedicated data leak site, in an attempt to name and shame them into deciding to pay. For Ransomware groups like Conti, the best outcome is when a victim pays quickly without alerting law enforcement officials because this makes the attack more difficult to track.
Based on this information I estimate the total of successful attacks by Conti at 200+ a month and I think that this is a conservative estimate.
How Double Extortion works and why it is effective
On March 27th, hackers attacked nine housing associations in my country (the Netherlands). The perpetrators (Conti) demanded a ransom, totaling 15 million euros. After payment, a decryption file would be sent and captured data would not be disclosed. The housing corporations were in contact with Conti and decided not to pay the ransom: their encrypted data was fully backed-up because of a good backup process. In their opinion, because no data was lost and servers could be up and running again very quickly no payment had to be done.
However, this is where “Double Extortion” came into play. Conti leaked 8GB of private data on the Dark Web from customers, including bank details, addresses, social security numbers, and copies of identity cards. The total amount of data stolen was estimated at 200GB. The housing associations were responsible for over 75.000 homes and information of all tenants was in Conti’s possession.
After publication, the housing associations got pressured by both tenants and authorities after which they started up negotiations again. Nothing was mentioned about these negotiations but within a day all leaked data disappeared from Conti’s website. This only happens when payment is done. Probably not the 15 million euro’s because the negotiation position was a bit stronger because the housing associations had all their data available because of a full back-up and a quick repair & clean process of their servers.
Still, the Double Extortion did its work and at least some payment was done. In Europe, data leaks of people are especially damaging for companies. On top of bad public relations, GDPR fines companies that breach privacy guidelines. Leaking private information (even not intended) is penalized by GDPR to a maximum of 4% of annual revenue.
The management panel
Conti’s subject management panes are mainly used for managing victims, affiliate accounts, and uploaded files. The Conti admin panel login page looks like this:
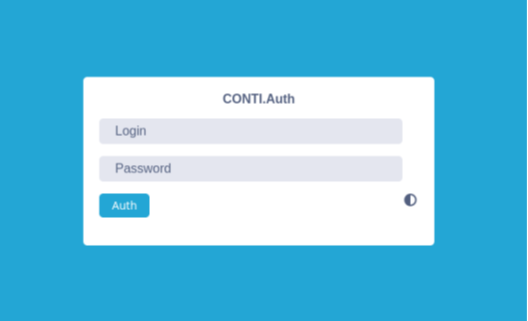
Conti’s affiliates create MEGA accounts, using the TOR browser to stay anonymous and use Bitcoin to pay Conti. After the payment, the Conti attackers upload data of the victim company to this account using the rclone tool as already discussed in a previous post.
Recruiting affiliates
Conti hires affiliates that do most of the work for them relating to customers. This is mainly managing the communication/negation process of the customer and the managing of the encrypted file (both providing samples and releasing it after payment has been done).
Affiliates are recruited from the deep web and darknet forums. Ransomware groups compete with each other to attract new affiliates into their network. Recruiters create topics in well-known forums and discussion boards to reach out to possible affiliates.
Becoming an affiliate requires great skills, motivation, and references from reputable cybercrime figures or organizations. It’s similar to offering your CV to a company in the ordinary business world.
Recruiting Ransomware groups are very secretive and selective in their recruitment process. Only members from experienced cybercrime organizations with a high reputation are recruited. The use of private communication channels in those organizations is mandatory. Posts and forum topics of Conti recruiters include penetration testing job ads and tooling projects most of the time. Conti prefers Russian-speaking affiliates which makes sense because Conti is Russian-based.
The Money Flow
Conti uses bitcoin payment as its main transaction method. 100+ bitcoin addresses are used for this. Its business model is Ransomware as a Service and because of this, RaaS transactions are split as the proceeds of each transaction are distributed between the ransomware operators and affiliates, with the exact percentage split differing between RaaS groups. Most of the time, the affiliates are awarded the majority of the ransom payment that is received. Ransomware operators tend to take a smaller percentage most of the time. However, Conti uses a slightly different model which looks more “wage-based” as opposed to a traditional RaaS payment model.
This wage-based approach surfaced with “The playbook leak” (part of the leaks beginning this year). Conti uses, at least in part, a lower-skilled and relatively low-paid workforce to gain initial access to systems, before handing off these “accesses” to more skilled team members. This approach allows the Conti operation to keep more (maybe even all) of the ransom proceeds for itself
This also might explain the many disputes about money between Conti and its affiliates/”employees” in the past. As in any other business, there are lots of internal struggles between employers and employees regarding the fairness of the wage that is being offered. Many times this ends in unsatisfied employees, internal struggles, and employees that leave a company angry and heartbroken. In some cases, an employee wants to damage their employer because they feel they have not been treated properly and to give the employer some payback. This also happens with cybercriminals, leaking source codes, IP addresses, etc.
How the Conti leak can help us in our defense against Cyberattacks
Bold cyberattacks continuously show our world how cybercriminals can impact the day-to-day business of many innocent people. Most of them are completely unaware of the fact that daily cyberwars are being waged between attackers and defenders. This is why it is important that people know how Ransomware groups like Conti operate in order to protect themselves and the people close to them against cyberattacks.
Awareness is a very important tool against cyber threats and helps in reducing the risk of exposure in the event of a possible attack.
Showing how the biggest Ransomware group out there operates (Conti), helps in creating more awareness and gives people a chance to arm themselves in order to prevent a successful attack by a Ransomware group. It also helps in forming a plan on how to act if you are successfully attacked, limiting the damage done.
Unfortunately, the cybercrime industry moves rapidly with a lot of ongoing technological and cultural changes. A good example of this is the introduction of cryptocurrency and the ongoing switch towards remote and hybrid work. This will significantly impact how cyberattacks occur in the near future in which Cloud computing and the exploit of its infrastructure by cybercriminals will have a pivotal role.
This means both public and private forces need to work together in order to improve the understanding of cyber threats. With an increase in understanding, risks can be mitigated which would decrease the legal and commercial impact of cybercrime.
The leaked Conti files provide a lot of insight into the inner workings of a cybercriminal organization, helping cybersecurity professionals, law-makers, and insurance companies to identify operatives and their external connections when investigating cybersecurity incidents.
Final Thoughts
“Know your enemy” is key in cybersecurity, and threat intelligence services gain lots of additional insight, helping in your defense against cybercriminals. In my opinion, this extra security layer is being ignored by a lot of companies but is indispensable in your preventive approach against cyberattacks. Threat intelligence enables companies to make comprehensive, data-based decisions about the overall exposure of their business by focusing on real-world threat actor tactics and techniques that are continuously evolving. This is far more effective than simulations, that is done once in a while.
And in the worst case, if there is no choice but to negotiate an enterprise that is equipped with state-of-the-art threat intelligence capabilities, have a much better chance of getting the upper hand, preventing critical damage to the brand, users, and stakeholders.
A final piece of advice: practice a Ransomware event at least two times every year based on a clear plan/scenario. A Disaster Recovery Plan (DRP) is key in this. By simulating Ransomware events, using a DRP, precious time (and money) is saved when a Ransomware event happens for real. The pressure on the company and its employees will be greatly reduced because both know how to act and how communication channels need to be managed. Panic is the biggest enemy during a Ransomware event and will lead to additional mistakes.
Feel free to contact me if you have any questions or if you have any additional advice/tips about this subject. If you want to keep in the loop if I upload a new post, do not forget to subscribe to receive a notification by email.





